云轴科技 ZStack Cloud
- Account Home
- Help & Support
- Training
ZStack Cloud provides VM instances with multiple network services, including VPC firewall, security group, virtual IP address (VIP), elastic IP address (EIP), port forwarding, IPsec tunnel, load balancing, OSPF area, Netflow, port mirror, and route table.
The Network Service Module provides a group of network services. Note that this module has been hidden on the UI.
Provides various network services: DNS, SNAT, load balancing, port forwarding, EIP, and DHCP.
ssh-key injection. By running cloud-init, these parameters will be loaded and injected into your VM instance when the VM instance is started. Note: The DHCP service includes the DNS feature.
Note: The DHCP service includes the DNS feature.ssh-key injection. By running cloud-init, these parameters will be loaded and injected into your VM instance when the VM instance is started. Note: The DHCP service includes the DNS feature.
Note: The DHCP service includes the DNS feature.ssh-key injection. By running cloud-init, these parameters will be loaded and injected into your VM instance when the VM instance is started.A security group provides security control services for VM instances on the L3 network. It filters the ingress or egress TCP, UDP, and ICMP packets of specified VM instances in specified networks based on the specified security rules.
 Note: If you specify both a CIDR block and a security group, only the ingress data from the intersection of the security group and CIDR block or egress data to the intersection of the security group and CIDR block is allowed.
Note: If you specify both a CIDR block and a security group, only the ingress data from the intersection of the security group and CIDR block or egress data to the intersection of the security group and CIDR block is allowed.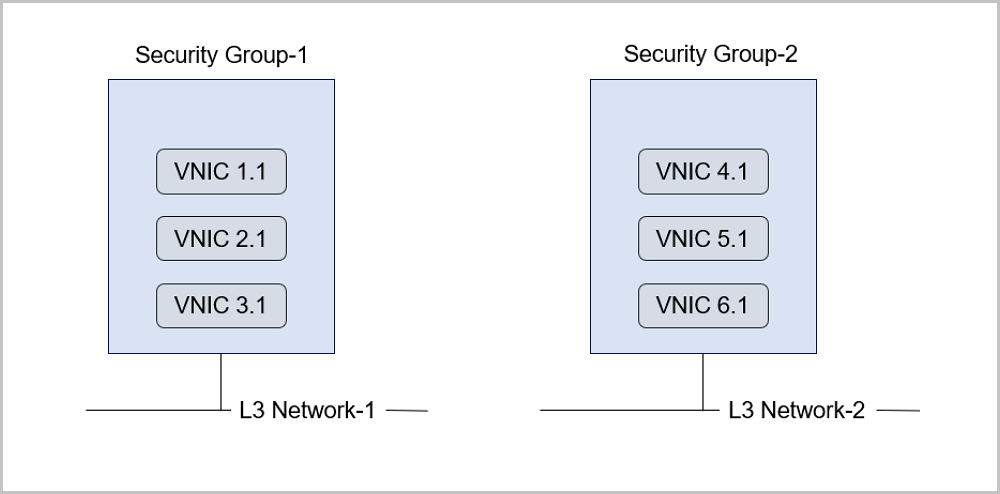
On the main menu of ZStack Cloud, choose . On the Security Group page, click Create Security Group. Then, the Create Security Group page is displayed.

Email Us
contact@zstack.ioEmail Us
contact@zstack.ioThe download link is sent to your email address.
If you don't see it, check your spam folder, subscription folder, or AD folder. After receiving the email, click the URL to download the documentation.Thank you for using ZStack products and services.
Submit successfully.
We'll connect soon.Thank you for choosing ZStack products and services.